The Des Moines metro is committed to creating an environment that…
Legendary UCLA Basketball Coach John Wooden knew a few things about winning. When he was asked about the key to building all of those championship teams he replied: “Any structure must have a strong foundation,” Wooden said. “The cornerstones anchor that foundation.”
As an IT leader one of the most important choices of your technology strategy surrounds the decision to go to the cloud and what vendor to partner with on this endeavor. While each business is unique as a Microsoft partner we’ve found that Azure is an excellent choice for many of our clients.
Azure is Microsoft’s Cloud Platform that has a wide variety of tools and solutions. From self-managed virtual machines to a hosted analytics platform, Azure has the tools to meet your technology needs. No matter what tool you want to utilize within Azure, by having a solid Azure foundation you will be able to easily maintain and expand your environment. Based on our experience here at Zirous here are some of the cornerstones that we find make up a solid foundation: naming and tagging standards, a defined hierarchy, a well-thought-out network design, and automated monitoring.
Naming and Tagging Standards
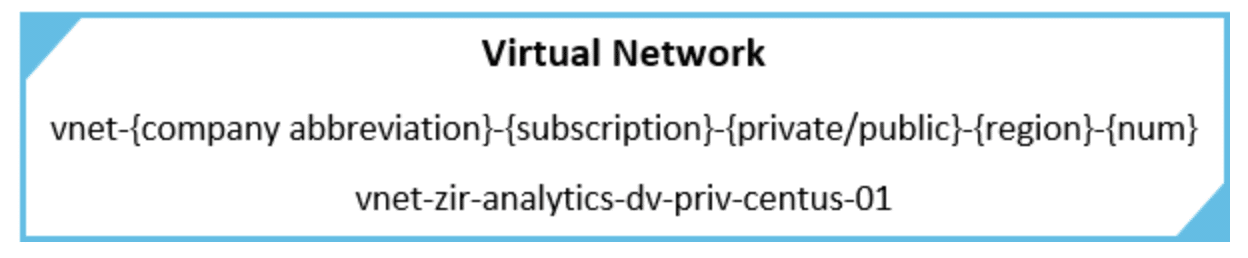
One of the most important cornerstones of the foundation is a well-defined and documented naming standard. Without these proper standards in place your environment can easily get out of control as it expands. Some resources within azure do not allow you to rename them after they are created, so making sure they have your desired name from the get-go can save you a lot of time and hassle. Azure has great documentation that gives an overview of naming conventions and another that lists resource abbreviations. You can use the Azure suggested naming convention or tweak it however you want. One thing that we have done here at Zirous is to tie every resource and resource group to the subscription name. If we have a subscription named analytics-dv-01 then we would want to include analytics-dv in the resource name as you can see in the example below.
Another important part of a solid foundation is having a tagging standard. While making tags are not required for your resources to function they can help organize and give insight into a particular resource. Tags also give you filter criteria so you can find exactly what you are looking for. If you want to utilize powershell or another scripting language, you can leverage the tags as variables. Azure breaks tags into 1 of 5 different categories; Functional, Classification, Accounting, Partnership, or Purpose. When creating custom tags determining which category they fit into will help keep the tagging structure organized. An organized tagging structure allows you to have an environment that can be easily navigated and maintained.
Hierarchy and Role Based Access Control
Once you know how to name everything you can start designing a hierarchy. When it comes to a good design, it would be ideal to make use of Azure’s organizational groups. That includes Management Groups, Subscriptions, and Resource Groups. Management Groups are at the top and only other Management Groups and Subscriptions can be put in Management Groups. Underneath that are Subscriptions, and only Resource Groups can be put in subscriptions. One thing to note is that you can nest Management Groups but can’t nest Resource Groups or Subscriptions. Below is a sample hierarchy utilizing all three organizational groups.
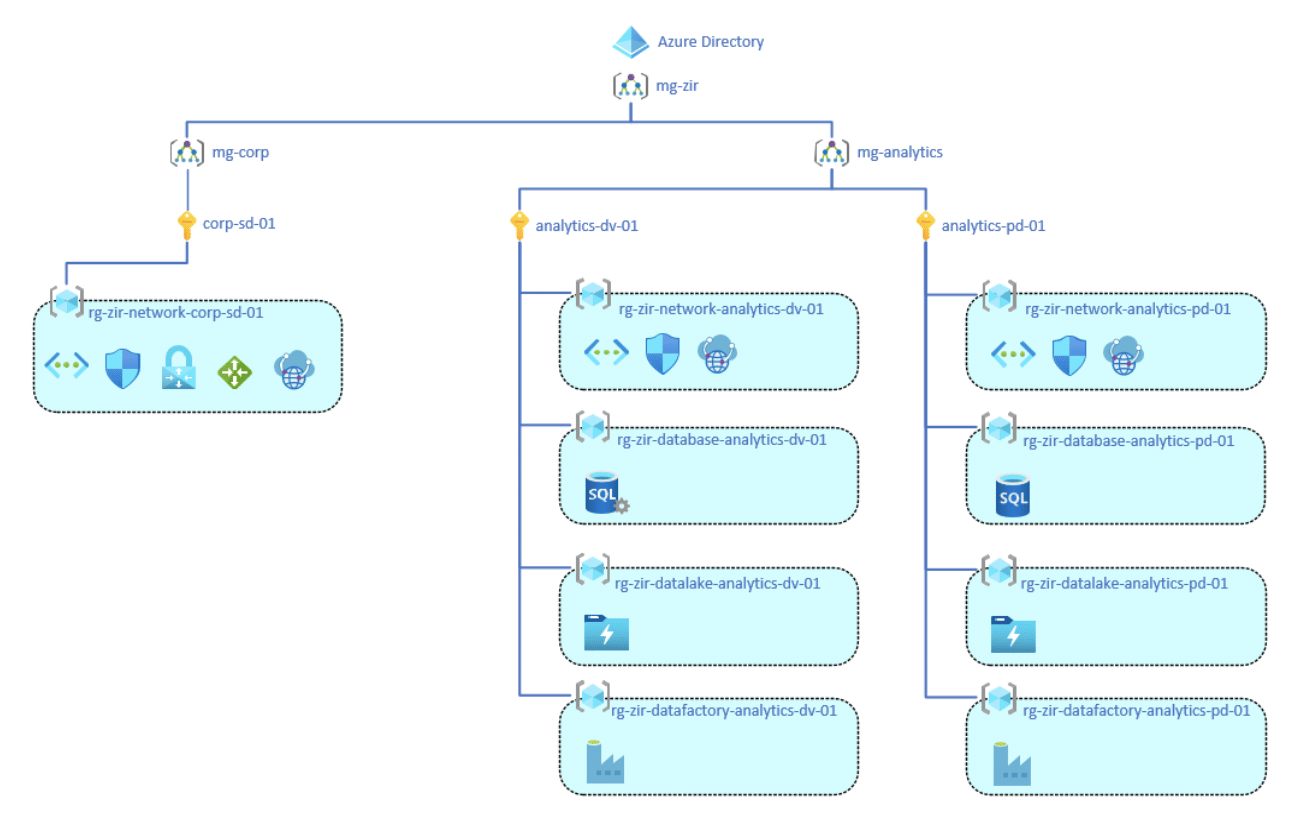
One Azure component that goes hand in hand with hierarchy is Role-based access control (RBAC). RBAC is the permissions you assign to your users or groups ensuring they have the proper access needed and nothing more. Azure has a large list of predefined roles that you can apply to your users or groups. You also have the ability to create a custom role from scratch or clone an existing role. You can assign roles in a variety of places, if you assign them to a particular resource they will only have access to that resource. When assigning roles to Management Groups, Subscriptions, or Resource Groups everything underneath them will also inherit the permissions. So using the example above, if you give a user permissions to the mg-analytics Management Group they will have that same permission on every resource under the analytics-dv-01 and analytics-pd-01 subscriptions.
Networking
Designing the Azure network to be both scalable and functional is a critical cornerstone of a solid cloud foundation. One of the most popular network designs within Azure is a hub and spoke model. Below is a simple example of this model, with one hub and two spokes. You can expand a simple model like that to include several different hubs and several unique spokes. Another important consideration when designing a network is IP address allocation. Your IP address will need to be unique between all connected hubs and spokes, as well as your on-prem if you want to connect it to Azure.
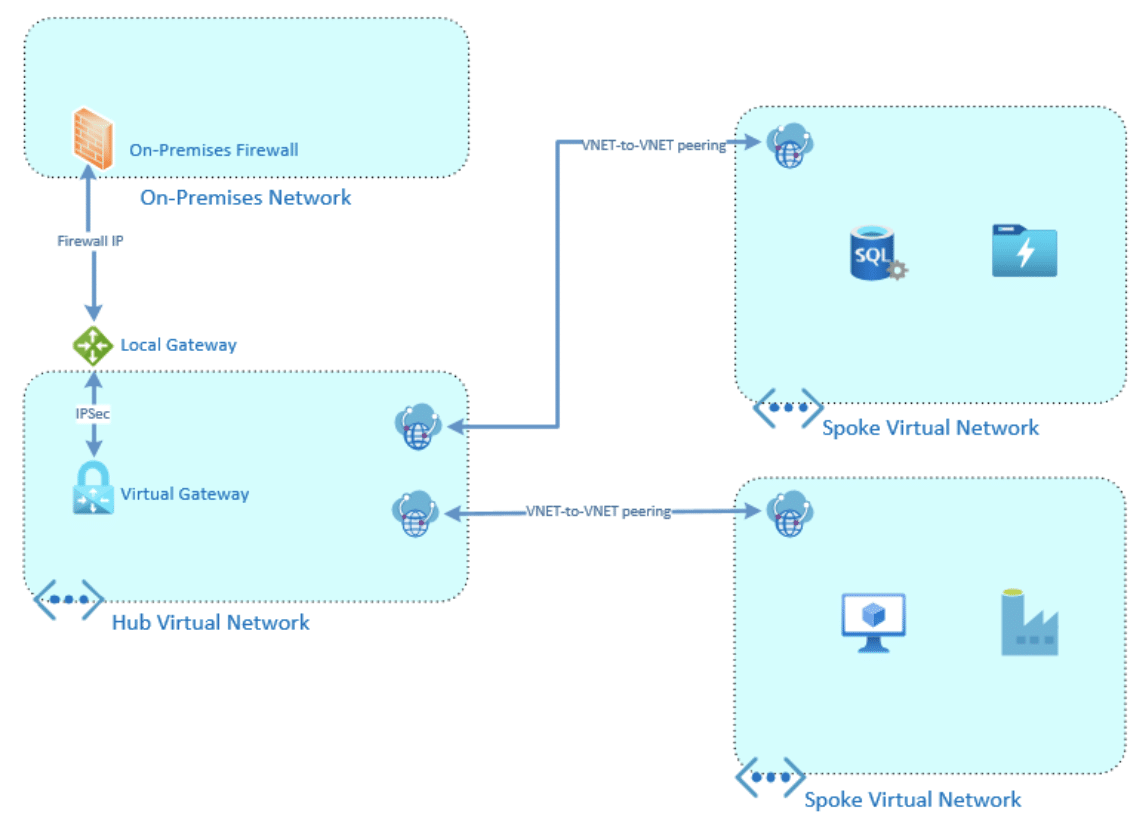
The main component in an Azure network design is the Virtual Network, or VNet. The Virtual Network is where the private IP address space is defined and where Subnets are created. Once you have a Virtual Network created you can start assigning resources to it. Any resource that requires a private IP will need to be tied to a Virtual Network with an available subnet. Some of the resources that rely upon Virtual Networks to get their private IP include; a Private Virtual Machine, An Azure PaaS using PrivateLink, or a Virtual Gateway. A Public IP is a separate resource that you can make and assign as needed.
If you want to connect a Virtual Network back to on-prem you have a couple of options. The easiest option is to set up an IPSec tunnel between a Virtual (VPN) Gateway and a Local gateway. Another option is a direct private connection between your Datacenter and Azure’s called ExpressRoute. There are also a couple of ways to secure your Virtual Network once it is created. The most basic way is an Access Control List (ACL) called Network Security groups, this is a standard allow/deny list based on IPs and ports. A more advanced consideration is the Azure Firewall, which functions as a traditional firewall within Azure, helping with both route management and improving security.
Monitoring
Once you have an environment up and running Azure has Monitoring and Alerting tools to help maintain your environment. Azure provides built-in metrics that vary depending on the type of resource, enabling you to use those metrics to monitor the health of your environment. You can also set up alerts if a specific metric crosses a defined threshold. As an example, if you have a VM you could set a threshold to get alerted if your CPU utilization is above 90% for 5 minutes. That example just scratches the service of the things you can do. If you want a deeper look into your environment you can create custom metrics or use Azure Monitor. Azure Monitor is a robust tool that brings together your metrics and resource logs, it allows you to gather insights and analyze all of our Azure resources to maintain maximum uptime.
The Right Partner for Azure
Azure is a leader in Cloud Infrastructure and has the tools to help your business succeed in the cloud. Having a solid foundation with the crucial cornerstones to build your Azure Environment allows you to make the most of those tools. And this is where Zirous comes in, Zirous is a Microsoft Partner with experience in implementing these foundations. We will provide more than just the implementation, we will work alongside your team to make sure they understand and are able to maintain the environment going forward. Zirous also has experts in the Analytics and Machine Learning sphere that can assist in the steps following. Contact us to see how Zirous can help you make the most of your environment.




This Post Has 0 Comments