Credential and Data Security Assessment
Proper data security begins with a strong foundation. Find out what you’re standing on with a deep-dive into the security of your Structured and Unstructured Data, Active Directory, and Windows infrastructure.

Enter to win a free assessment!
UNCOVER CRITICAL CREDENTIAL AND DATA RISKS
DATA
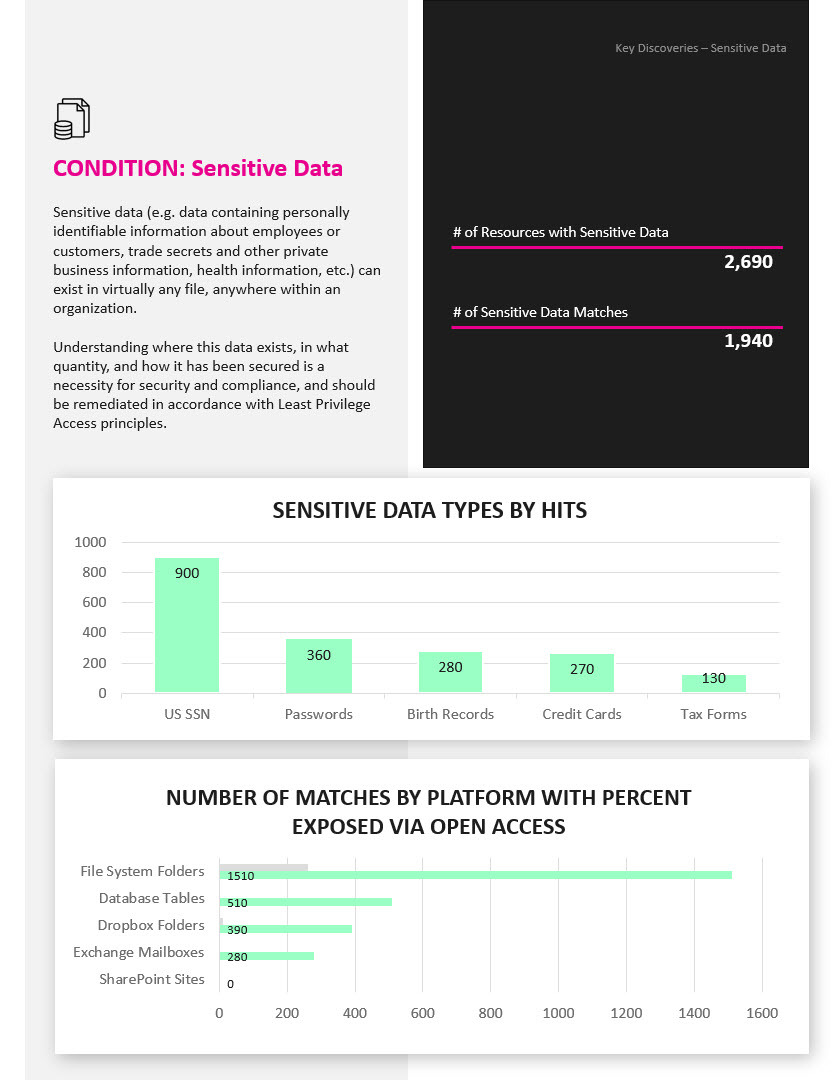
Discover sensitive data, open access rights, high-risk permissions, and stale data that is putting your organization at risk.
CREDENTIALS
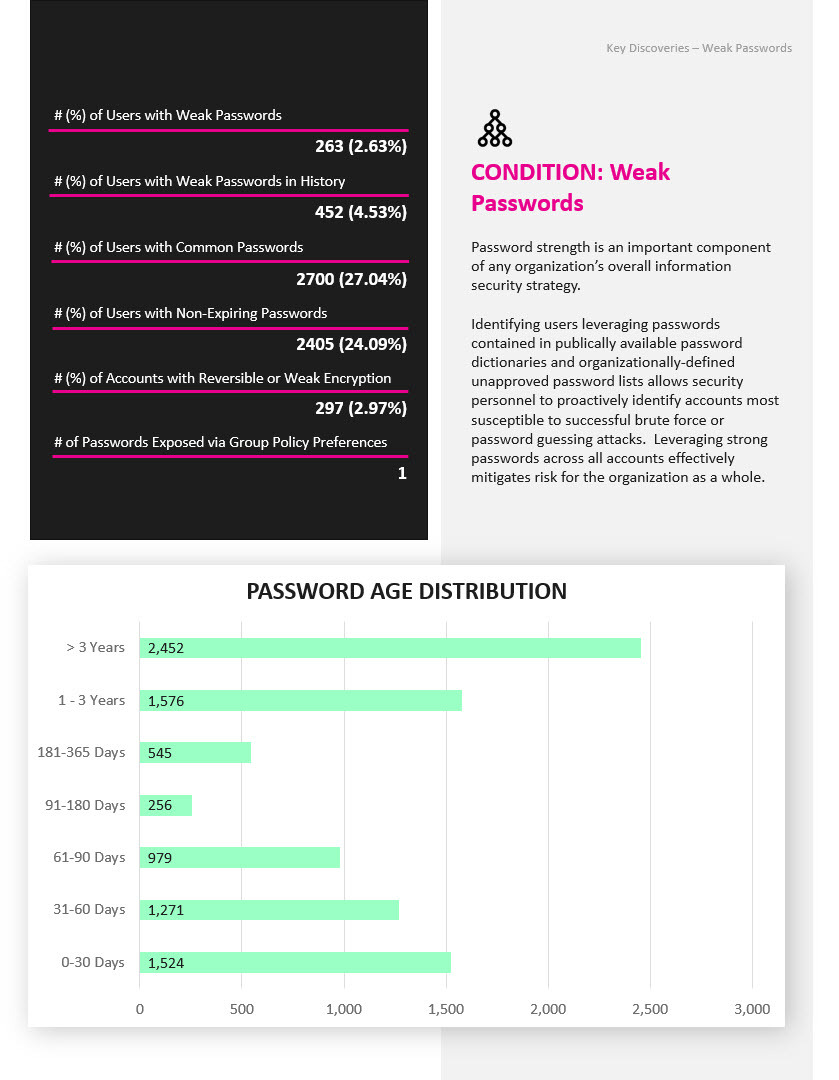
Pinpoint vulnerabilities in Active Directory permissions, account passwords, privileged access rights, configurations, objects, and more.
SYSTEMS
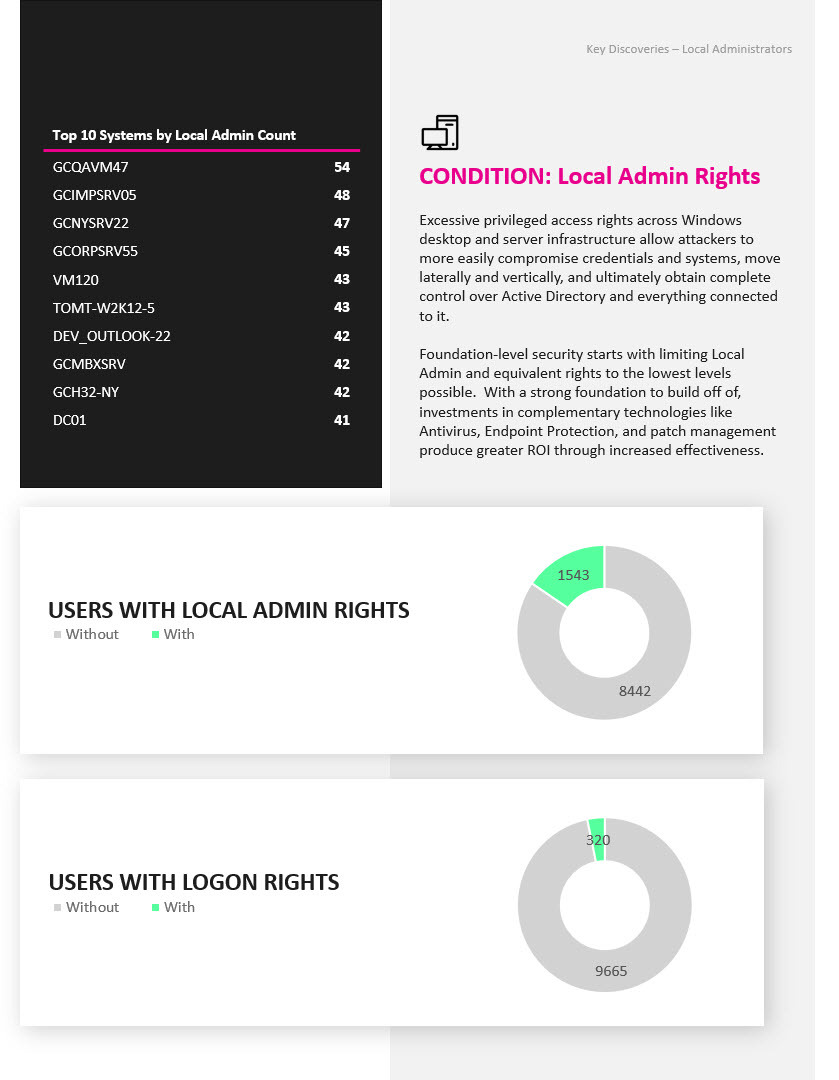
Identify privileged access rights, service accounts, critical misconfigurations and conditions attackers exploit to steal credentials.




