Keeping company data safe is a top priority in a fast-paced…
In recent months, the workplace landscape has witnessed a drastic change. With an increasing amount of remote workers, data breaches are on the rise and system safeguards are now more essential than ever. Reports state that cybercrime cases have quadrupled since the COVID-19 pandemic and the focus of attacks have changed. Prior to the pandemic, small businesses were the primary targets of attack but now major corporations, government institutions, and infrastructure are suffering. One stage of attack is a lateral movement, where an invader attempts to gain access to high level privileges by moving from one compromised user or machine to another throughout a system. This juncture of an attack can be detrimental when unnecessary privileges exist. Fortunately there are precautionary measures your corporation can take, such as the implementation of a Privileged Access Management (PAM) system. Traditional PAM helps prevent these attacks by keeping passwords complex and minimizing their exposure to admins during sessions, but it’s not enough because that privileged access still exists for attackers to compromise.
While PAM software has been around for nearly 20 years, newer functionalities can not achieve their capabilities when applied to decade old platforms. Stealthbits has taken the lead in defining a new approach to traditional PAM by advocating ephemeral accounts to achieve true just-in-time access and eliminate standing privileges. This approach drastically reduces attack surface, compared to traditional PAM implementations.
The Modern Approach to PAM
As award-winning experts in the field and a cybersecurity solutions provider, Stealthbits has renovated the PAM experience. SbPAM, StealthBits Privileged Activity Manager, provides cutting edge technology. In order to help ensure customers maximize the SbPAM experience, Zirous is a proud Stealthbits partner and able to provide clients full implementation support and professional services. Director of Research & Technology, Ryan Babbitt said that SbPam extends other Zirous offerings in the identity and access management space.
“We thought it important to partner with StealthBits because of the vision and breadth of their security portfolio,” Babbitt said. “StealthBits provides data access governance to both structured and unstructured data in a number of systems, next-generation privileged access management, and strong Active Directory security and threat mitigation, which provides a complement to our existing expertise in Identity and Access Management.”
The SbPam Experience
Stealthbit’s SbPAM separates itself from competitors in its implementation and compliance ease, flexibility, and cost. Zirous has partnered with this cutting edge technology in order to ensure that clients are able to take full advantage of the features offered by providing implementation support, sizing/scaling, and other professional services.
PAM, and SbPAM specifically with its focus on activity-based security, adds to your IAM program in two important ways. First, it provides visibility, control, review, and approval over local and privileged access in domains, servers, and workstations, particularly when that access is ephemeral and exists only for a short time. This type of access does not traditionally fall under the scope of IAM solutions. Second, it provides a framework to implement the governance best practice of least privilege by enabling companies to transition from a bloated dual-account access model to a leaner, more efficient, and more secure zero-standing privilege paradigm.
As a consultant charged with advising and implementing this product for customers, I’ve become intimately familiar with the SbPam tool. SbPAM certainly sets itself apart from competitors, but I was most impressed with:
- The ease of installation and use
SbPAM is very proud of their ease of use, even stating that single server installation time can be up and running in as little as 20 minutes. Amazingly, as a first-time user I was able to have SbPAM installed and running in under two hours. Aside from easy installation, the installation guide is easy to follow and keeps things moving swiftly and smoothly. It is easy to tell that Stealthbits wanted to ensure that clients did not have to deal with complex and lengthy installations. This pairs well with the other options provided by SbPAM, allowing for easy scaling and simple integration with other PAM products through the Bring Your Own Vault (BYOV) technology,providing the option to complement existing PAM products or land and expand a new PAM program.
- Its use of activities to move the industry forward
In addition to the installation process, I was also impressed with how easy it was to create activities using SbPAM. Activities are another way in which Stealthbits sets itself apart from its competitors. Traditional PAM solutions have focused on privileged escalation and management, whereas SbPAM has taken a new, more modern approach to PAM by focusing on activities and session goals.
But what are activities? As previously mentioned activities and activity tokens are SbPAM’s new take on PAM. Unlike traditional PAM solutions SbPAM creates accounts and provisions permissions for those accounts on a per session basis, as needed to support the current activity. This approach follows the principles of “just in time access” and “zero standing privilege”. Since accounts are created and managed per session, users only have enough access to perform the requested actions. Since accounts are deleted after use, there is no standing privilege left behind for malicious actors to leverage. SbPAM can even clear security session tokens such as Kerberos tickets to keep them from being used in attacks.
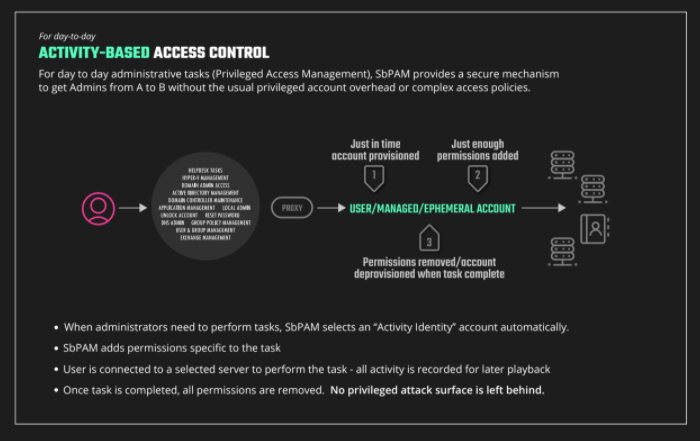
Activities in Figure 1, above, not only help to create a more secure environment but are also extremely easy to implement. This simplicity reduces user error and unnecessary vulnerabilities. Stealthbits have greatly reduced the likelihood of these errors through their straightforward, simple, and user friendly system.
- An Informative Training Experience
To sum up my experience working with SbPAM in one word I would go with “Impressive”. I would describe SbPam as a five star, user friendly experience with informative software that provided top level security. Each step of the way, as I gained more mastery in the field, it was easy to see that SbPAM was shaped with their users in mind.
True Technology Partners
While SbPAM provides the aforementioned implementation and user experience, like many modern software solutions, its ROI really depends on how well it is used. For example, how can one move from the installation phase into best practice use? What challenges would one face implementing SbPAM in an environment that already has other governance tools? Are there other tools that pair well with this software to create a total protection package? These are the questions that Zirous can help answer.
Zirous partners with Stealthbits to ensure customers utilize SbPAM to its full experience. With full implementation support and professional services, Zirous will enable a secure comprehensive governance and compliance program. Set up a free demo and let Zirous ease and transform your security infrastructure.



This Post Has 0 Comments