Keeping company data safe is a top priority in a fast-paced…
It is obvious that there are many benefits of cloud computing. Don’t worry, I am not going to document them here because that has already been done many times. By now, you already realize what the cloud has to offer and are well on your way to digital transformation. Instead, I want to focus specifically on one aspect of cloud computing that still presents many challenges – Identity Governance. No matter which stage of the transition you may find yourself, having a plan to manage identity security is important.
Who accessed what and when?
Cloud providers typically include some sort of identity management features within their offerings. However, these features are usually basic and only apply to users managed in that particular cloud space. Many companies have found it necessary to keep some legacy infrastructure onsite and utilize one or more cloud providers to handle other parts of their remaining business infrastructure. This adds complexity and makes it difficult to manage different sets of user bases in a consistent, best practices manner. Coupled with increasing compliance and regulatory requirements, managing identity security and understanding “who accessed what and when” can become extremely complicated for a company of any size when adopting cloud technologies.
AWS IAM Example
When looking at Amazon Web Services, the included AWS IAM features offer a good starting base for managing identity security in their cloud offering. Administrators have the ability to manage users, groups, roles, and policies within their AWS organizations. There are also built-in reporting capabilities to track how users are interacting with cloud components. However, AWS IAM does have some shortcomings. First, it only provides a limited visibility to answer the question of “who accessed what and when.” Also, there is an overall lack of a unified approach to identity governance using AWS IAM. It is missing common features such as being able to request, approve, and certify access. Not having these basic governance features can potentially lead to accidental mismanagement and/or misconfiguration, especially in larger implementations. Gartner has estimated that “80% of cloud breaches will be due to customer misconfiguration, mismanaged credentials, or insider theft, and not cloud provider vulnerabilities”. Ultimately, AWS IAM is missing some of the established identity governance best practices, but that can be remedied.
Bring on SailPoint IdentityIQ
When adding the power of SailPoint IdentityIQ to the basic IAM capabilities included with AWS, you can allow AWS resources to be secured and governed consistently with the rest of your infrastructure. IdentityIQ also improves the effectiveness of governing AWS by providing many added capabilities. Information from AWS IAM is simply imported into IdentityIQ through an aggregation process, and this allows complete management of AWS cloud resources from the IdentityIQ UI – the same as all other IT resources.
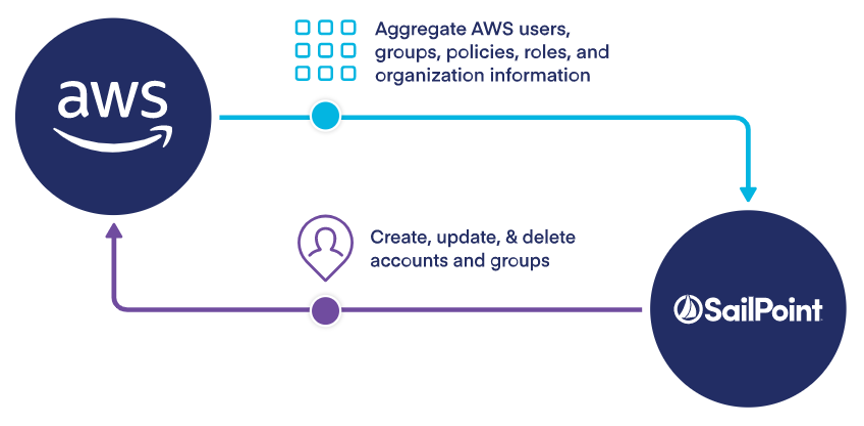 IdentityIQ’s centralized view provides the ability to see access to all of the applications, servers, storage, and databases running on your AWS account. IdentityIQ also provides the following identity governance benefits to AWS:
IdentityIQ’s centralized view provides the ability to see access to all of the applications, servers, storage, and databases running on your AWS account. IdentityIQ also provides the following identity governance benefits to AWS:
Full Identity Lifecycle Support
IdentityIQ provides full provisioning capabilities for IAM users, groups, and policies. End users get the ability to make access requests for AWS policies from the same console they would use for access to other company infrastructure, applications, and data. These requests can be associated with approval workflows ensuring confidence that the access is permitted and necessary. Finally, access certification of policy content and membership assignments is included.
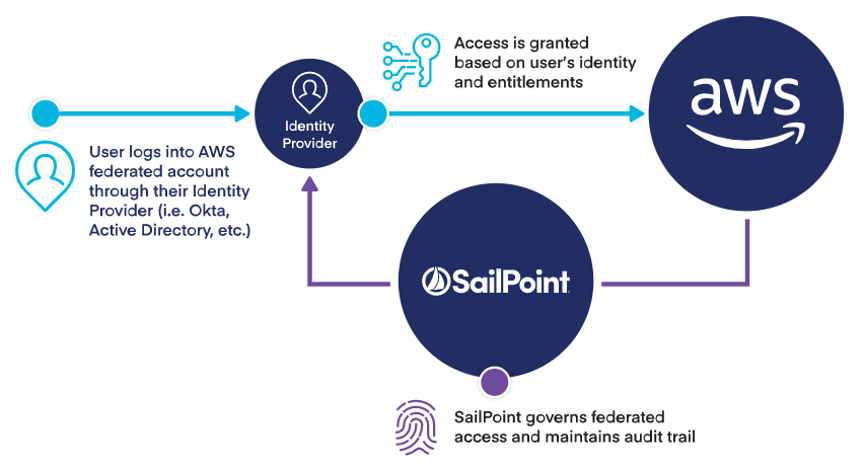
Federation Mapping
Improved support for managing federated access between your company’s directory service and AWS helps reduce account and entitlement sprawl, improving overall governance. Fewer accounts and entitlements to manage means there will be lower administration overhead and reduced risk. Existing company identities can be used to grant secure and direct access to SailPoint AWS resources without having to make a brand new AWS identity for those users.
 Separation of Duties Policies
Separation of Duties Policies
Decrease security risks by creating SoD policies to prevent dangerous and toxic combinations of AWS roles, groups, policies, and permissions. This helps eliminate undesirable access from being provisioned to AWS users and groups.
Automatic Credential Rotation
Keys, secrets, and passwords can be automatically rotated after each use to help limit risk.
Deep Policy Support
Identify and evaluate dynamic condition elements that may exist within an AWS policy. This provides improved visibility and control. Ultimately, greater assessment capabilities make it easier for managers to review access and ensure that users can only access the information they need to do their job.
Policy Snapshot History
This capability provides accurate audit trails of “who accessed what and when.” User policy history within AWS shows the version and condition element values of the policy at the time of access, providing context during access certification.
Let Us Help
Zirous is an experienced strategic partner who can help you achieve your governance goals. Let us help using our combination of experience and strong partnerships with Oracle, SailPoint, and Okta to provide value to your organization. Together we can position your company to be prepared for all challenges you may face with identity security.



This Post Has 0 Comments