Storage Reclamation
StealthAUDIT helps you lower storage costs by automatically moving stale resources to cheaper disks in compliance with policies around each class of data. StealthAUDIT helps you identify outdated sensitive or regulated information and safely remove it through cold archiving or deleting.

COMPANIES ARE PAYING FOR 60% MORE STORAGE THAN THEY NEED
Gartner found that in 2019 the average annual storage cost per raw TB of capacity was $7381, and the average number of raw TBs supported per storage FTE is 4,1681. With organizations using only 40% of stored data, this adds up to a lot of wasted expense, and that figure doesn’t even take into account the cost of maintaining storage, which runs another $111k to $164k in IT labor hours a year.
Regulated information covered by Sarbanes-Oxley Act (SOX), the Health Insurance Portability and Accountability Act (HIPAA), Payment Card Industry (PCI) and new regulations protecting privacy like CCPA, will require better security protection and faster retrieval than data that is not regulated or sensitive. You need to figure out:
What information is regulated?
How frequently each will be accessed?
How long to keep each type of information?
If you don’t want to keep the data – what to do about it?
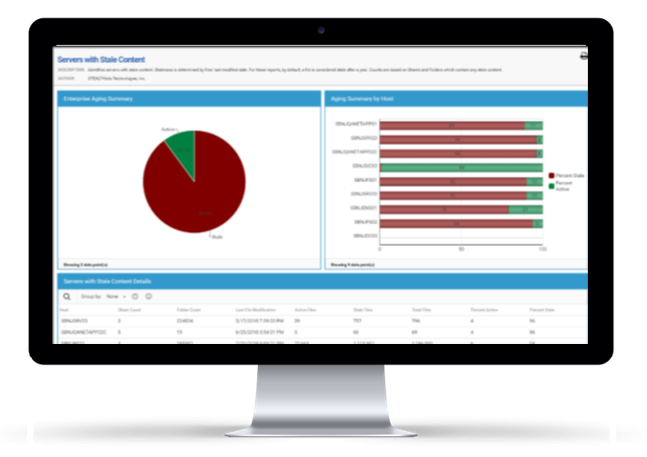
StealthAUDIT Delivers...
See how StealthAUDIT can save you time and money when it comes to Storage Reclamation.






